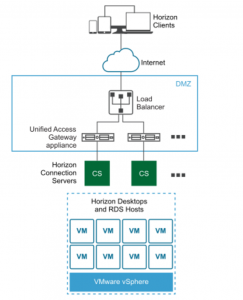
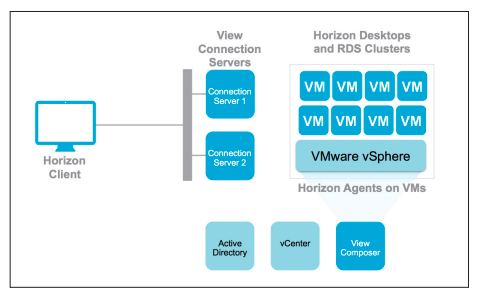
Current situations accelerate the demand for virtual desktops and a proper virtual desktop infrastructure. I am working for years in the field of the software-defined datacenter and virtual desktops delivered via VMware Horizon. While standard office virtual desktops have become something like a commodity, the usage of hardware graphics accelerated workload and high-end demand is still kind of ‘newer’ and not as mature as the non-gpu workload.
I am involved in a large scale product that creates a virtual desktop landscape for engineers doing a lot computer aided engineering (CAE). This is a very interesting environment that comes with a lot of difficult user requirements and how it can be solved.
- 3D Acceleration required during normal “working” operations when modelling / analyzing components. (NVIDA vGPU for the win)
- Huge amount of local persistent storage to cache models loaded/checked out from a network location. (vSAN is everywhere in the cluster, included in Horizon Advanced & brutal fast if you do it right).
- High throughput between the virtual desktops and the network location (The big benefit of a VDI setup).
- Secure access from everywhere & sharing of the session (Another big benefit of VDI).
- Windows & Linux Desktops must be supported (Horizon can do that)
- Huge amount of memory per virtual desktop since sometimes models can have 100/200GB of size and needs to resist in the memory of the virtual machine. (vSphere scales indefinelty [almost :P]).
- Most engineers will require a dedicated linux desktop where he can individually use modules/kernels/packages based on his needs (an IT managements nightmare). (dedicated user assignment with persistent VDIs).
- Different working behaviours (more than 500 different user-interaction scenarios) that cannot easily be matched to a single use-case.
- Store certain states of the virtual desktop. Loading / pre-processing might take 1-XX hours and needs to be repeated several times (VM snapshots with memory ftw).
- Certain Desktops should be shared among team-members (working in parallel or sequential).
- …..